Introduction
Some corners of the internet aren’t just dark, they’re bulletproof.
While most of us associate web hosting with blogs, online stores, and the occasional cat video archive, there’s an underground ecosystem that operates with a very different set of rules. It’s a place where malware servers thrive, takedown requests die quietly, and digital fugitives find safe haven behind encrypted walls. Welcome to the shadowy world of bulletproof hosting.
Bulletproof hosting, or BPH, in cyber lingo, refers to a form of web hosting designed to resist legal scrutiny, government takedowns, and abuse reports. It’s not just flexible on content restrictions; it’s practically allergic to them.
In this blog, we’ll take a deep dive into what bulletproof hosting is, how it differs from traditional hosting, who uses it (and why), and the growing concerns surrounding its role in modern cybercrime. We’ll also explore some infamous examples and shed light on why this murky niche continues to thrive despite global crackdowns.
Bulletproof Hosting, Explained
At its core, bulletproof hosting is internet infrastructure with an attitude.
Bulletproof hosting (BPH) refers to web hosting services that turn a blind eye, sometimes willfully, to the legality of what’s hosted on their servers. From phishing sites to ransomware command centers, bulletproof hosts specialize in shielding shady online operations from interference, often operating in jurisdictions where cybercrime laws are either weak, unenforced, or openly manipulated.
Unlike conventional hosting providers who uphold legal and ethical standards, Bulletproof hosts build their business model on non-compliance. They’re the digital equivalent of a safehouse, no questions asked, no logs kept, and no cooperation with law enforcement.
A Brief Origin Story
The concept of bulletproof hosting dates back to the early 2000s, when cybercriminals began outgrowing hobbyist tools and needed more robust, evasive infrastructure. One of the earliest and most infamous players was the Russian Business Network (RBN), a hosting provider known for facilitating phishing, identity theft, and botnet operations with impunity.
Since then, bulletproof hosting has evolved from obscure forums and IRC channels into a multi-million-dollar underground economy. Today, these hosts operate with far more sophistication, offering encrypted backends, rotating server clusters, and payment options in crypto to ensure full anonymity.
And in a digital age defined by surveillance, censorship, and rising cybercrime, bulletproof hosting has found itself at the controversial intersection of free speech and felony, making it both a vital tool and a dangerous weapon, depending on who’s wielding it.
Key Characteristics of Bulletproof Hosting
When it comes to bulletproof hosting, the devil isn’t just in the details; it’s in the design. These operations are built from the ground up to dodge scrutiny, silence takedowns, and shelter content that would be vaporized in seconds on mainstream platforms. Here’s what sets them apart:
Extreme Content Leniency
Forget terms of service. Bulletproof hosts allow everything, from phishing kits and ransomware payloads to illicit pornography, counterfeit product sites, and dark web storefronts. If it can be monetized or weaponized online, it’s welcome here.
Legal Resistance and Jurisdictional Games
Bulletproof hosting thrives in legal grey zones. These providers often establish operations in countries where cybercrime laws are ineffective, outdated, or ignored. When takedown requests land, they’re met with silence or a redirect to a non-existent legal department.
Anonymity on Steroids
Real names? Verified IDs? Not in this neighborhood. Bulletproof hosts pride themselves on allowing clients to stay completely anonymous. No KYC checks. No paper trail. Just an IP address and a crypto wallet.
Constant Infrastructure Relocation
BPH providers don’t stay in one place for long. To avoid detection and coordinated takedowns, they often move their servers across borders, continents, or into underground networks. Entire infrastructures can vanish overnight, only to resurface hours later on a different ASN.
Crypto-Only Payments & Privacy Layers
From Bitcoin to Monero, bulletproof hosts lean hard into cryptocurrency to keep transactions untraceable. Add on tools like bulletproof VPNs and decentralized DNS, and you’ve got a ghost operation with no visible operator.
Bulletproof vs Conventional Hosting
Two hosting worlds. One plays by the rules, the other rewrites them in disappearing ink. Here’s how they stack up:
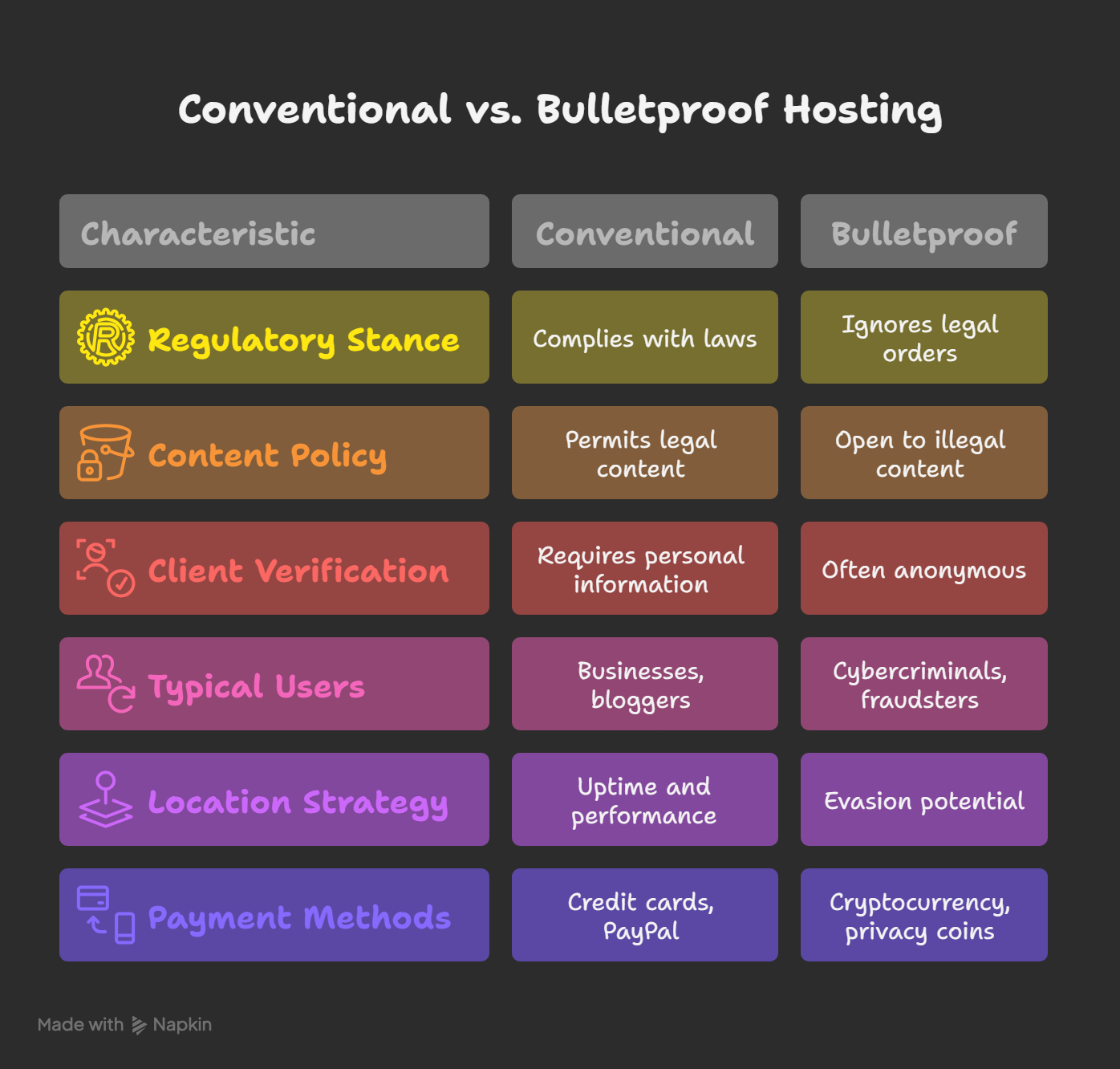
The takeaway? While conventional hosts work to protect the web, bulletproof hosts help exploit it. And for the bad actors of the internet, that makes all the difference.
Why People Use Bulletproof Hosting
Not all users of bulletproof hosting wear digital ski masks, but many do. From career cybercriminals to political outcasts, the motivations for using BPH are diverse. Some seek shadows to exploit. Others seek refuge. Let’s break it down:
Cybercrime Operations: Where BPH Truly Thrives
At its most notorious, bulletproof hosting is the digital backbone of cybercrime. Think:
- Phishing campaigns that mimic legitimate banks and harvest credentials
- Botnet command-and-control (C2) servers that quietly puppet networks of infected machines
- Ransomware gangs who need a place to stash payloads and extortion infrastructure
- Spam kings pushing everything from counterfeit meds to fake crypto schemes
BPH gives these actors something priceless: time. Time to operate before takedowns, time to scale operations, and time to vanish without a trace.
Political Dissidents vs Digital Pirates: A Murky Middle
Not everyone in the bulletproof universe is a villain. In some regions where free speech is criminalized, political dissidents and whistleblowers turn to bulletproof hosting to protect controversial or censored content. It’s rare, but real.
Still, there’s a fine line between censorship resistance and crime sanctuary. And in many cases, that line gets blurred, if not obliterated, by copyright pirates, fake news peddlers, and extremist propagandists who exploit the same platforms.
Shielding Content from Legal Takedowns
Bulletproof hosting is a digital fortress for anyone trying to dodge:
- DMCA notices
- Copyright strikes
- Content moderation bots
- Platform bans
That’s why it’s popular among torrent indexing sites, illegal IPTV providers, and underground marketplaces. If you don’t want your content yanked offline, and you don’t mind skating the edge of legality or plunging past it, BPH is your best bet.
Risks and Ethical Dilemmas
Behind the promise of unfiltered freedom lies a landmine field of risk. Bulletproof hosting may sound invincible, but it comes with heavy baggage, including legal, ethical, and operational.
Legal Risks: Who’s Coming After You?
Make no mistake: using BPH for illegal activity puts a bullseye on your back.
- International task forces (like Europol and INTERPOL) coordinate cybercrime crackdowns
- ISPs and hosting watchdogs often blacklist IP ranges associated with bulletproof providers
- Cross-border legal action is slow but increasingly effective — and when it lands, it hits hard
While many providers claim immunity based on location, international law is catching up. Think you’re safe because your server’s in Moldova? Think again.
The Intent Dilemma: Is All Use Unethical?
Is a BPH user always a bad actor? That’s the question.
- Hosting a political blog critical of an oppressive regime? Possibly noble.
- Hosting pirated Netflix content on that same server? Not so much.
Intent matters, but perception is everything. And in a world where guilt by association is common, even ethical users risk collateral damage from being on a “dirty” host.
Operational Risks: The House Might Burn Down
- No customer support.
- No service guarantees.
- Frequent “exit scams,” where the host disappears with your data or money.
- Uptime instability, especially if the provider is constantly migrating to avoid detection.
You may be renting space in a fortress, but it might be one built on quicksand.
Notorious Case Studies
If bulletproof hosting had a Mount Rushmore of infamy, these two would be carved in stone:
Russian Business Network (RBN): The OG Syndicate
Arguably the first and most feared name in bulletproof hosting, the Russian Business Network (RBN) exploded onto the cybercrime scene in the mid-2000s. Based in Russia, it offered a safe harbor for:
- Phishing operations
- Identity theft rings
- Malware distribution
- DDoS-for-hire services
What made RBN stand out? Blatant defiance of law enforcement and a near-impenetrable web of proxies, shell companies, and international jurisdictions. At its peak, RBN powered a significant portion of the global cybercrime economy.
McColo: The Spam Empire That Fell
McColo was a U.S.-based hosting provider that unwittingly (or not) became home to:
- Some of the world’s largest botnets (including Srizbi and Rustock)
- Massive spam operations
- Child exploitation content and credit card theft forums
When it was finally shut down in 2008, global spam volume dropped by over 60% overnight. That moment marked one of the first high-profile bulletproof takedowns and showed the world just how central these providers were to the cybercrime pipeline.
Other (Dis)Honorable Mentions
- CyberBunker (Netherlands): Famous for its “we host anything except child porn and terrorism” policy
- Host Sailor (UAE): Frequently accused of harboring fraud sites and malware
- Offshore Racks (Multiple): An elusive, rotating BPH provider linked to dark web marketplaces
- Kamatera, Yalishanda, and Ecatel: All named in multiple cybercrime investigations over the last decade
The Bigger Picture
Bulletproof hosting isn’t just a shady footnote in cybersecurity; it’s a cornerstone of the digital underground. In the cat-and-mouse game of internet crime, BPH providers are the fortified bunkers, giving bad actors the time and cover they need to scale attacks. Ransomware gangs? Hosting payloads and leak sites via bulletproof infrastructure. Phishing campaigns? Spinning up fake bank portals that last longer than they should. DDoS crews? Commanding botnets that bounce signals across these resilient networks.
A Moving Target for Law Enforcement
Despite major takedowns, bulletproof hosting continues to evolve. Law enforcement faces:
- Legal loopholes across borders
- Jurisdictional stalemates
- Anonymous transactions via crypto
- Rapid server mobility and decentralization
Even when a provider is identified, the infrastructure often reboots elsewhere under a new name, new IP, and fresh DNS. It’s whack-a-mole, but the mole has mirrors.
Bulletproof Hosts and the “CaaS” Revolution
There’s also a shift happening: Cybercrime-as-a-Service (CaaS). BPH has become part of a larger stack, alongside plug-and-play ransomware kits, credential marketplaces, and fraud tutorials. For as little as $200/month, anyone — regardless of skill — can rent space on a bulletproof server and launch attacks with enterprise-grade tools.
The bottom line? Bulletproof hosting is no longer niche. It’s infrastructure.
Conclusion
Bulletproof hosting exists at the volatile intersection of innovation, exploitation, and evasion. It’s not just a technological loophole, it’s a moral one.
While a sliver of its user base may be fighting censorship or surveillance, the overwhelming reality is darker: bulletproof hosts are foundational enablers of cybercrime. They are the unseen scaffolding behind phishing attacks, ransomware campaigns, and digital fraud on a global scale.
As governments and tech platforms try to keep pace, the game continues to evolve, and so do the players.
So the next time you hear about a breach, a shutdown, or a takedown, know this: behind many of those headlines is a server, somewhere, running bulletproof.
And it’s still online.





0 Comments