Introduction
In the ever-evolving world of cybersecurity, programming is not just an optional skill—it’s essential. Whether you’re writing custom scripts, developing exploits, or automating repetitive tasks, a strong grasp of programming can set you apart as a penetration tester. In this article, we’ll explore the most valuable programming skills every security pro should master, ensuring you’re well-equipped to tackle today’s sophisticated threats.
Core Programming Languages for Security Experts
Mastering these languages provides a strong foundation for understanding vulnerabilities, creating tools, and developing exploits.
Python: The Swiss Army Knife for Hackers
Python’s simplicity and powerful libraries make it indispensable for cybersecurity. It’s widely used for scripting, building security tools, and automating tasks.
Why Python Is Essential:
- Simplicity and Readability: Easy for beginners and versatile for complex tasks.
- Extensive Libraries: Tools like
Scapyfor packet crafting andSocketfor network programming. - Applications in Penetration Testing: Create tools for scanning, fuzzing, and automation.
Examples:
- Writing scripts for network scanning.
- Developing custom payloads and exploits.
- Automating data collection from targets.

C and C++: The Power Behind System-Level Access
For deeper system-level understanding, C and C++ are essential. They allow security pros to manipulate memory directly, making them invaluable for developing exploits and understanding vulnerabilities at the system level.
Key Benefits of C and C++:
- Low-Level Operations: Ideal for developing rootkits and analyzing system processes.
- Memory Manipulation: Crucial for exploit writing, buffer overflow attacks, and reverse engineering.
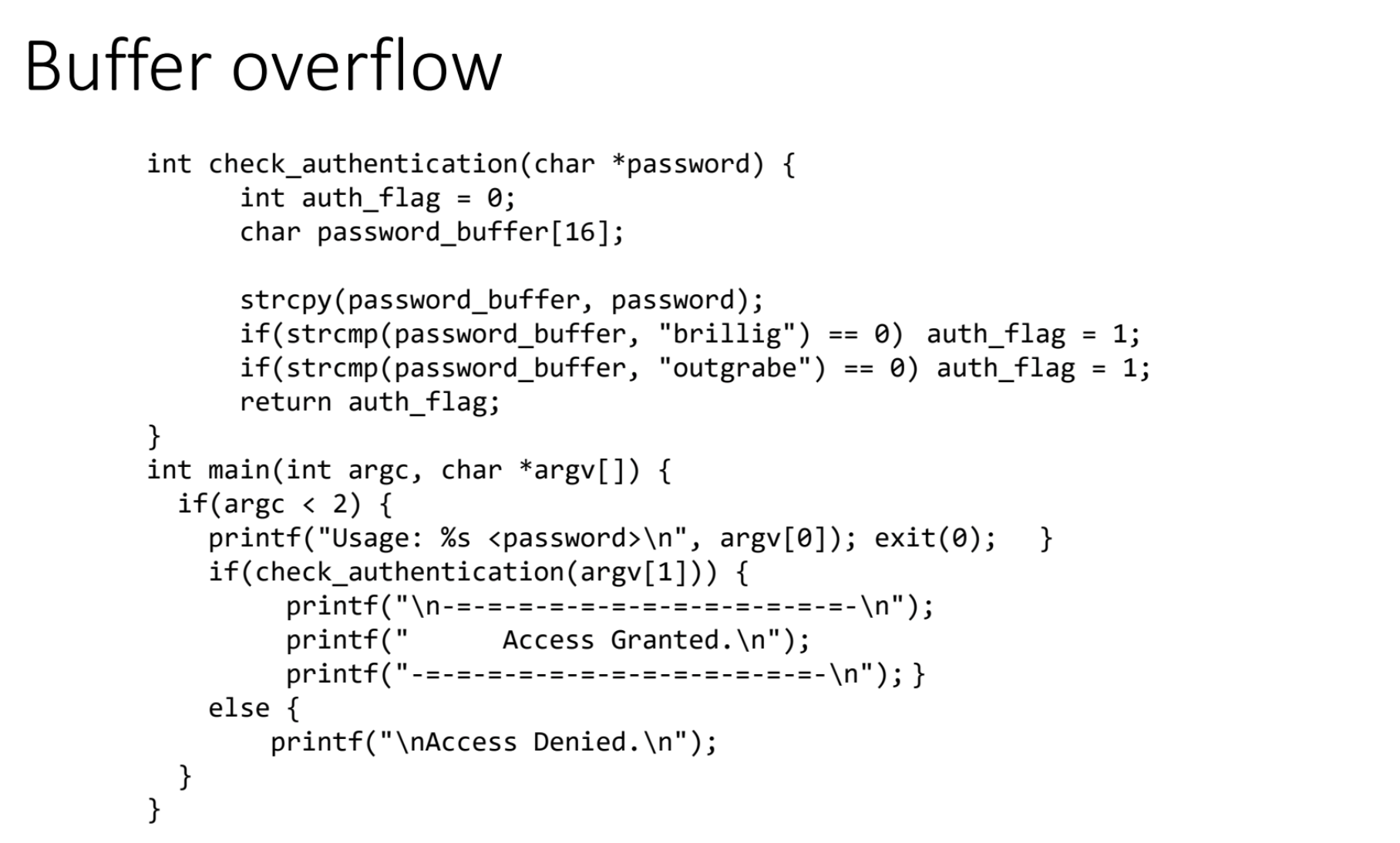
JavaScript: The Web Security Essential
JavaScript is the backbone of web applications and is often exploited by attackers. Mastering JavaScript helps you identify web-based vulnerabilities and develop client-side attack simulations.
Applications in Cybersecurity:
- Testing for XSS Vulnerabilities: Create proof-of-concept attacks to assess client-side security.
- Web Application Security: Understand and test web apps for potential weaknesses.
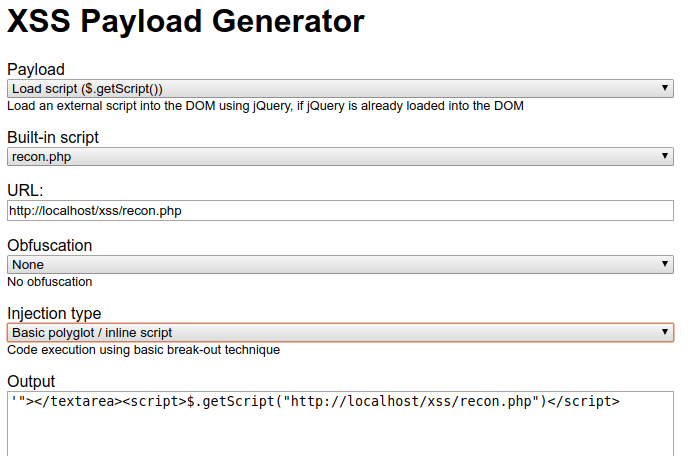
Bash and PowerShell: Command Line Power Tools
For automation and efficient execution of commands, knowing Bash (for Unix systems) and PowerShell (for Windows) is critical. These scripting languages streamline penetration testing tasks and are essential for working within command-line environments.
Why Command-Line Scripting Matters:
- Automating Repetitive Tasks: Save time by scripting routine checks and scans.
- Windows and Linux Exploitation: PowerShell is particularly powerful for exploiting Windows environments, while Bash is integral for Linux-based operations.

Specialized Programming Skills for Penetration Testing
a. Scripting for Reconnaissance and Automation
Creating scripts that automate data collection and reconnaissance tasks is invaluable. Python and Bash scripts can be written to search for open ports, gather data, or scan for vulnerabilities.
Practical Applications:
- Develop scripts that automate OSINT (Open Source Intelligence) collection.
- Create automated network mapping tools.
Writing Exploits and Payloads
Exploit development is a key part of penetration testing. Knowledge of C and Python allows you to create custom payloads and exploits tailored to specific vulnerabilities, helping you demonstrate potential attack methods.
Tips for Developing Exploits:
- Start with simple proof-of-concept codes.
- Understand how to manipulate memory and bypass security protections.
- Utilize exploit development platforms like Metasploit for guidance.
Reverse Engineering Skills
Reverse engineering involves deconstructing software to understand how it works and identify vulnerabilities. Security professionals use tools like Ghidra and IDA Pro, but programming knowledge enhances these efforts by allowing in-depth analysis.
Why Reverse Engineering Is Vital:
- Dissect malware to understand behavior and intentions.
- Identify potential vulnerabilities in proprietary software.
- Assist in creating patches for vulnerabilities.
Web Application Testing Scripts
Building custom scripts to test for vulnerabilities like SQL injection, XSS, and CSRF ensures that penetration testers can tailor their approach to different web applications.
Approaches to Custom Scripting:
- Write scripts that automate vulnerability checks.
- Build scripts for brute force and dictionary attacks.
- Create scripts that test the security of form submissions and API endpoints.
Understanding Code Review and Debugging
Reviewing code is a proactive way to detect vulnerabilities before attackers find them. Security pros should know how to spot common coding flaws, such as unvalidated inputs or improper use of libraries.
Key Techniques for Effective Code Review:
- Analyze third-party code and identify weak points.
- Spot common coding vulnerabilities like insecure deserialization.
- Debug custom tools to ensure accuracy and security.
Practical Tips for Learning Programming as a Security Pro
Learning programming can be daunting, but these steps can make it manageable:
Actionable Tips:
- Choose the Right Path: Begin with Python for its ease of use, then move to C for system-level programming.
- Practice by Building Projects: Create simple tools such as a web scraper or a basic network scanner.
- Collaborate on Open-Source Projects: Contribute to security-focused GitHub projects to gain real-world experience.
Recommended Tools and Resources
Equip yourself with the best tools and resources to maximize your learning:
Top IDEs:
- VS Code: Versatile for many languages.
- PyCharm: Excellent for Python development.
- Sublime Text: Lightweight and powerful.
Essential Libraries and Frameworks:
- Requests (Python): Simplifies HTTP requests.
- pwntools: A CTF framework for writing exploits.
Learning Platforms:
- Hack The Box: Challenges to test penetration skills.
- TryHackMe: Step-by-step cybersecurity training.
- Codecademy: Interactive programming lessons.

Conclusion
Programming skills are what separate highly effective penetration testers from the rest. By mastering the right languages and applying them through real-world projects and testing, cybersecurity experts can sharpen their skills and stay ahead of attackers. Keep learning, keep practicing, and push your limits to be the best in the field.





0 Comments