Google operates the most widely used search engine globally, systematically scanning and indexing web pages from across the internet to construct an immense database of digital content. Typically, users tap into this database by entering keywords to locate articles or websites pertinent to their interests. Google’s proprietary algorithm, PageRank—named after co-founder Larry Page—organizes the search results by relevance, ensuring the most authoritative sources appear prominently.
However, beyond basic searches, Google offers specialized keywords and operators that enable users to pinpoint highly specific information within its vast repository. For hackers, these advanced techniques, often termed “Google hacking,” can unlock valuable insights about potential targets, including sensitive data like passwords, without ever directly engaging the target’s systems.
Google Hacking Keywords
Google’s advanced search capabilities hinge on operators that refine queries when paired with a colon (:) and specific terms. Below are some commonly used examples:
| allinanchor | If you use the allinanchor keyword, Google restricts your search to those web pages that have ALL of the terms you are looking for in the anchor of the page. |
| alllintext | If you use the allintext keyword, Google restricts your search to those pages that have the search terms you specify in the text of the page. |
| allintitle | If you use the allintitle keyword, Google restricts your search to those pages that have ALL of the search terms you specify in the title of the page |
| allinurl | If you use the allinurl keyword, Google restricts your search to those pages that have ALL of terms you specify in the URL of the page. search |
| filetype | If you use the filetype keyword, Google restricts your search to those pages that have the filetype you specify. For instance, to search for an Adobe PDF file, you could use filetype: pdf |
| inanchor | If you use the inanchor keyword, Google restricts your search to those pages that have search terms you specify in the anchor of the page. |
| intext | If you use the intext keyword, Google restricts your search to those pages that have the search terms you specify in the text of the page. |
| intitle | If you use the intitle keyword, Google restricts your search to those pages that have the search terms you specify in the title of the page. |
| inurl | If you use the inurl keyword, Google restricts your search to those pages that have the search terms you specify in the URL of the page. |
| link | When you use the link keyword followed by the URL Google shows you all the sites that link back to the specified URL. |
| ext | Searches for a specific file extension. |
| cache | Displays the cached version of a page as it was indexed by Google. |
| phonebook | Searches for phone numbers and contact information for a specific person or business. |
| map | Displays a map of a specific loacation or address. |
| related | Displays webpages related to a specific URL. |
| info | Provides information about a specific website, including its cache, similar pages, and pages that link to it. |
| define | Displays the defination of a specific word or phrase. |
| site | If you use the site keyword, Google restricts your search to the site or domain you specify. |
Practical Examples of Google Hacking
Google hacking shines when these operators are combined to uncover precise information. Here are some illustrative scenarios:
Finding Excel Files with Sensitive Data
Many organizations store critical details—like financial records or contact lists—in Excel files. A query like filetype:xls will locate such files. To narrow it further, combining operators can yield targeted results. For instance:
- filetype:xls site:gov inurl:contact searches government websites (.gov) for Excel files with “contact” in the URL, potentially revealing lists useful for social engineering.
- filetype:xls inurl:email.xls seeks Excel files explicitly named with “email,” likely containing address lists.
Identifying Vulnerable Web Applications
Certain PHP-based applications are prone to exploits like SQL injection. A search such as inurl:index.php?id= can reveal sites using this common URL structure, flagging potential vulnerabilities for further investigation.
Locating Administrative Pages
Queries like intitle:”site administration:please log in” may uncover login portals for website administration, offering entry points for unauthorized access attempts.
Gathering Personal Information
For social engineering, a search like intitle:”curriculum vitae” filetype:doc can retrieve Word documents containing resumes, rich with personal details about individuals.
Exposing Unsecured Webcams
Google hacking can also locate unprotected webcams online. Effective queries include:
allintitle: “Network Camera NetworkCamera”
intitle:”EvoCam” inurl:”webcam.html”
intitle:”Live View / – AXIS”
intitle:”LiveView / – AXIS” | inurl:view/view.shtml
inurl:indexFrame.shtml “Axis Video Server”
inurl:axis-cgi/jpg
inurl:”MultiCameraFrame? Mode=Motion”
inurl:/view.shtml
inurl:/view/index.shtml
“my webcamXP server!”
These often reveal live feeds from cameras lacking proper security, showcasing a lighter, yet intriguing, application of these techniques.
Expanding the Arsenal: Google Dorks
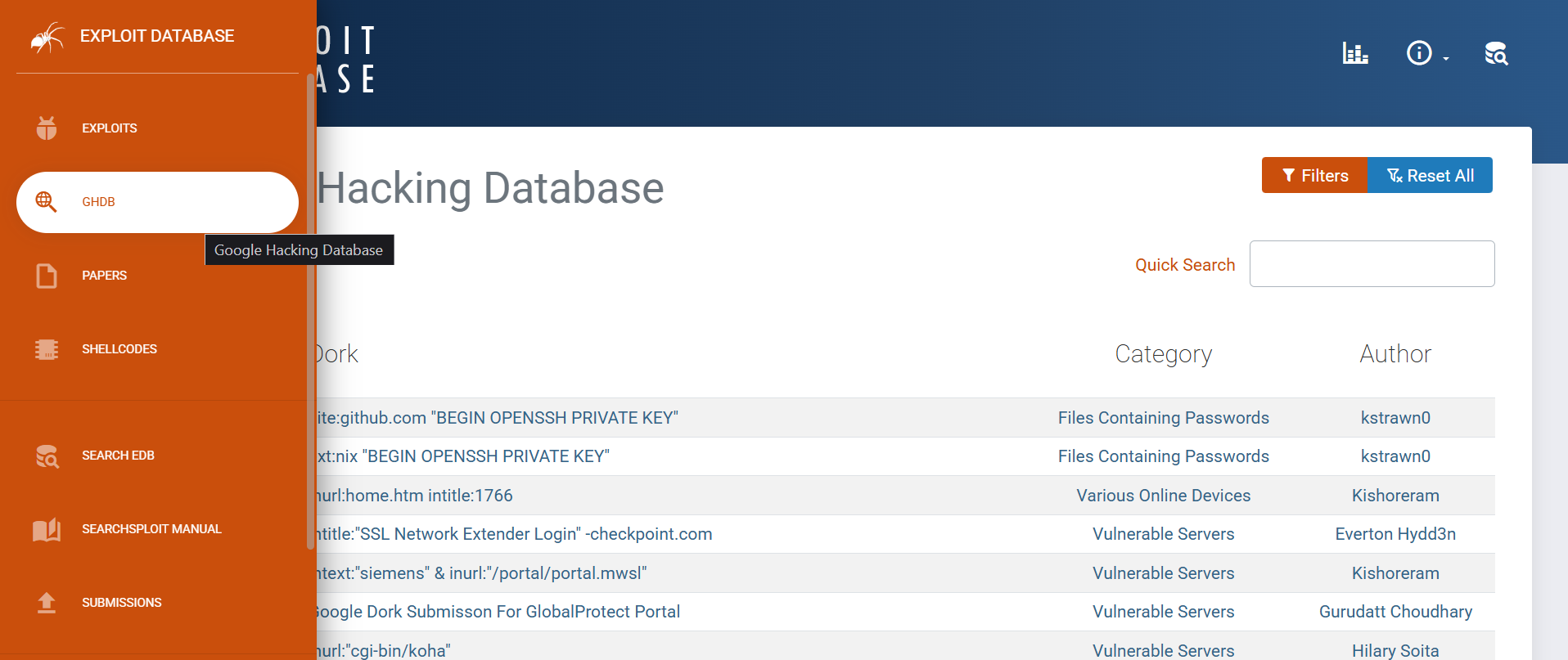
The examples above are just the beginning. Known as “Google dorks,” these pre-crafted search queries are extensively cataloged by experts like Johnny Long, a pioneer in the field who has authored books on the topic. Another rich resource is the Exploit Database, where the “GHDB” (Google Hacking Database) tab provides thousands of dorks. Users can filter these by specific targets—such as WordPress sites—by entering relevant keywords into the search tool.
A sophisticated example from the GHDB might be:
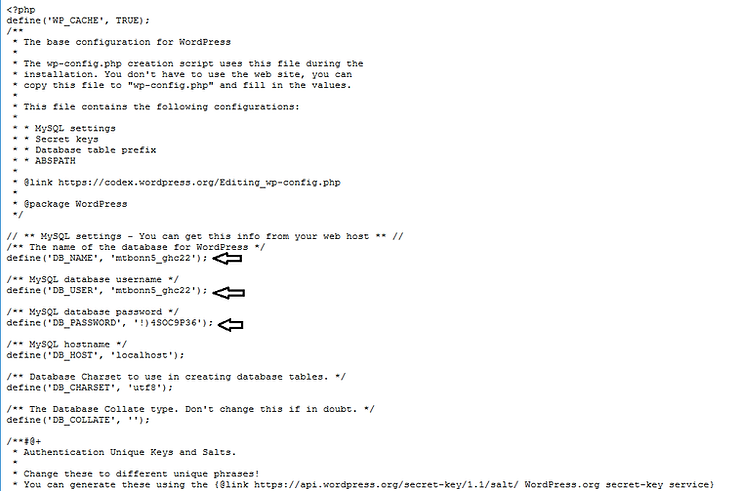
filetype:sql intext:password | pass | passwd intext:username intext:INSERT INTO `users` VALUES
This query hunts for SQL scripts that include terms like “password” and “username” alongside database insertion commands. Executing it could reveal scripts exposing actual username-password pairs, simplifying account compromise.
Why Google Hacking Matters
Mastering Google hacking is a vital skill for hackers, offering a passive yet potent method for reconnaissance. By leveraging publicly available data, hackers can amass critical intelligence—such as contact details, system vulnerabilities, or credentials—without directly probing a target’s infrastructure. This approach minimizes the risk of triggering security mechanisms like Intrusion Detection Systems (IDS), saving time and effort in the information-gathering phase of a project.
Each hacking endeavor is unique, requiring tailored techniques. While not every Google dork will apply to every target, the ability to adapt and refine these queries ensures hackers can efficiently extract the most relevant insights from Google’s unparalleled database, making it an indispensable tool in their toolkit.





0 Comments