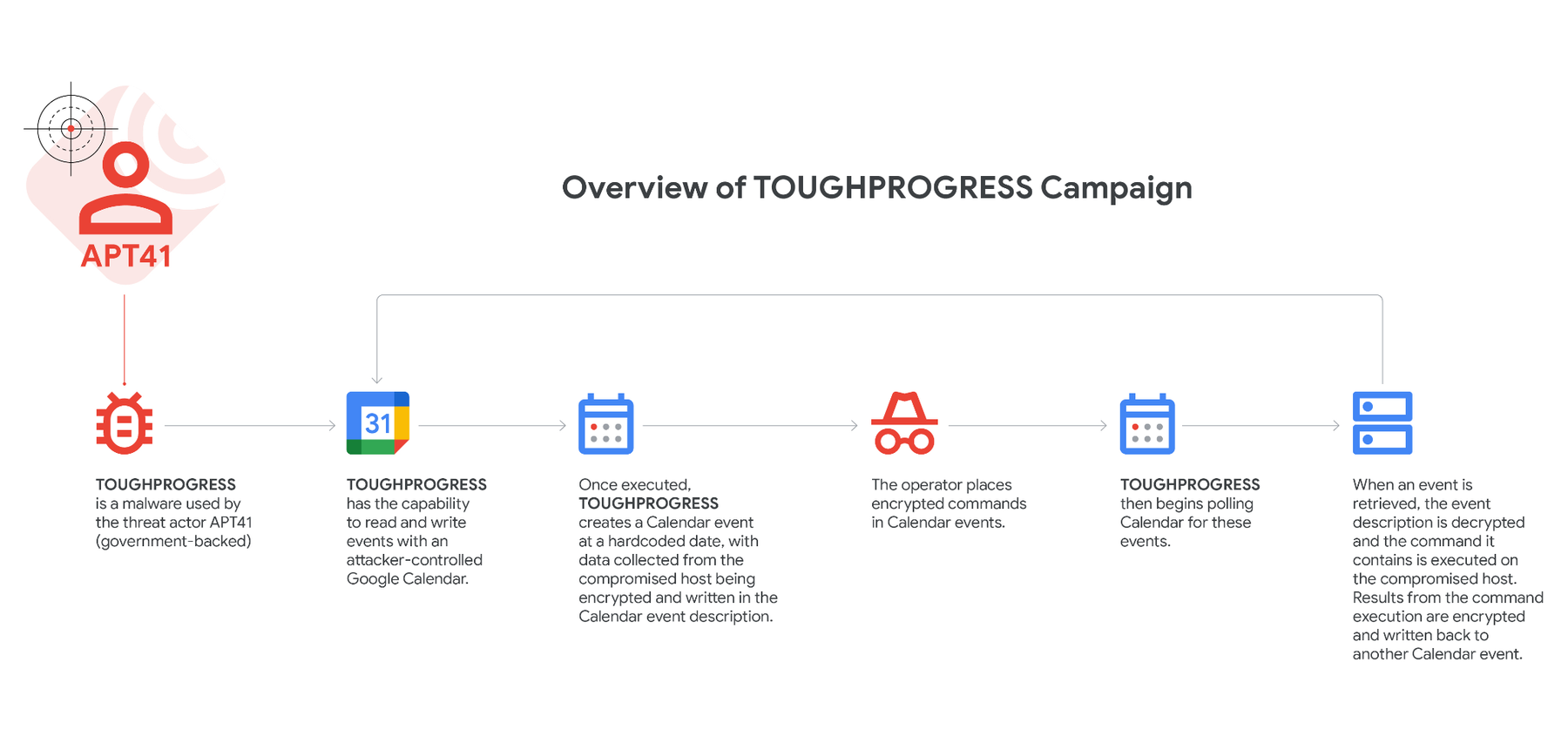
Google has uncovered that the Chinese state-sponsored hacking group APT41 has been using a custom malware strain, dubbed TOUGHPROGRESS, to exploit Google Calendar as a command-and-control (C2) channel. This tactic enables the attackers to blend in with legitimate cloud-based activity, making detection more difficult.
The campaign, which Google identified in late October 2024, involved the malware being hosted on a compromised government website. The malicious software was then used to target various other government bodies. According to Patrick Whitsell from Google’s Threat Intelligence Group (GTIG), leveraging cloud services for C2 communications is a common strategy among advanced threat actors aiming to remain inconspicuous.
APT41, also known by several other aliases including Axiom, Wicked Panda, Brass Typhoon, and Winnti, has a well-documented history of targeting key sectors such as government, logistics, media, technology, and automotive industries. In July 2024, Google reported a prolonged cyber-espionage campaign by the group against organizations in Italy, Spain, Taiwan, Thailand, Turkey, and the UK, using various tools such as web shells and malware droppers like ANTSWORD, BLUEBEAM, DUSTPAN, and DUSTTRAP.
Earlier, in March 2024, a subgroup within APT41 was linked to cyberattacks against Japanese companies in sectors including manufacturing and energy, in a campaign identified as RevivalStone.
The most recent attack involved spear-phishing emails containing links to ZIP files hosted on an infiltrated government site. These ZIP files included a directory and a deceptive Windows shortcut (LNK) disguised as a PDF. Inside the directory were seven images labeled from “1.jpg” to “7.jpg”, two of which were disguised malware components.
When the LNK file is activated, it displays a fake PDF document that claims to require species export declarations. However, the “6.jpg” and “7.jpg” files are fake images; one is an encrypted payload, and the other is a DLL that decrypts and executes the malicious code when triggered.





0 Comments