Introduction Some corners of the internet aren’t just dark, they’re bulletproof. While most of us associate web...


Introduction Some corners of the internet aren’t just dark, they’re bulletproof. While most of us associate web...
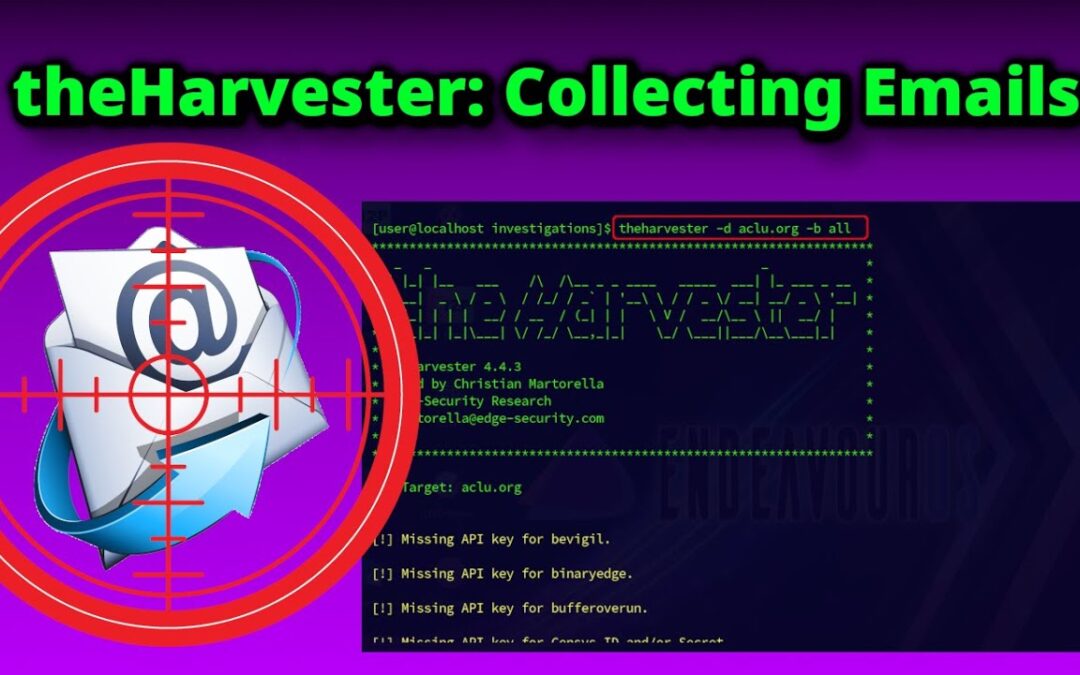
When it comes to gathering email addresses during OSINT investigations, theHarvester is among the most efficient and...

With the dramatic rise in the value of cryptocurrencies in recent years, theft in this space has surged accordingly....
At first glance, hiring a hacker to secure your information systems might seem counterintuitive, even risky. After...
For some time, I’ve been considering writing an article on why hacking is the most critical skill set in today’s...
SCADA (Supervisory Control and Data Acquisition) and ICS (Industrial Control Systems) differ significantly from...
The escalating tensions between Russia and Ukraine have reignited debates about the role of cyberattacks in modern...
For individuals with a background in traditional IT or IT security, stepping into the world of SCADA (Supervisory...