With this new blog series, I intend to examine several of the most significant hackers of the 21st century. The goal is to draw lessons from their...
Blog & Articles
Cybersecurity News, Latest Vulnerabilities, Hacking Tutorials
Understanding the Hacker Methodology
Many inexperienced hackers misunderstand the structured process required to carry out a successful intrusion. Instead of following a disciplined...
Supply Chain Attack Hits Popular npm Packages
Security researchers have identified a sophisticated supply chain attack that infiltrated several widely used npm packages. The breach was...
What is Bulletproof Hosting?
Introduction Some corners of the internet aren’t just dark, they’re bulletproof. While most of us associate web hosting with blogs, online stores,...
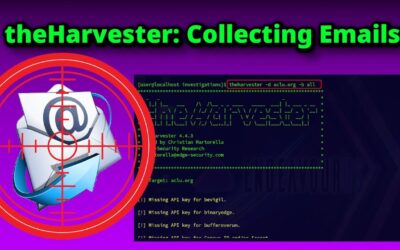
Extracting Email Addresses with theHarvester
When it comes to gathering email addresses during OSINT investigations, theHarvester is among the most efficient and beginner-friendly tools...
OSINT: Using Reverse Image Searches in Investigations
The internet holds a vast amount of data, and with the right tools and techniques, nearly anything can be uncovered. One powerful method in the...
Discover How We Can Protect Your Assets
Reach out to learn how Ouroboros Security can address your cybersecurity challenges. Call us, send an email, or complete the contact form below to begin securing your organization today.