
by Noel Saido | Feb 24, 2026 | Hackers
With this new blog series, I intend to examine several of the most significant hackers of the 21st century. The goal is to draw lessons from their experiences and help you develop a wider understanding of your chosen discipline. The first profile focuses on the...

by Noel Saido | Feb 4, 2026 | Hacking, Penetration Testing
Many inexperienced hackers misunderstand the structured process required to carry out a successful intrusion. Instead of following a disciplined approach, they often rush directly to exploitation without completing the necessary groundwork to ensure the attack...

by Noel Saido | Jul 22, 2025 | News
Security researchers have identified a sophisticated supply chain attack that infiltrated several widely used npm packages. The breach was facilitated by a targeted phishing operation that successfully stole authentication tokens from package maintainers, granting...

by Noel Saido | Jul 10, 2025 | Cybersecurity, Hacking
Introduction Some corners of the internet aren’t just dark, they’re bulletproof. While most of us associate web hosting with blogs, online stores, and the occasional cat video archive, there’s an underground ecosystem that operates with a very different set of rules....
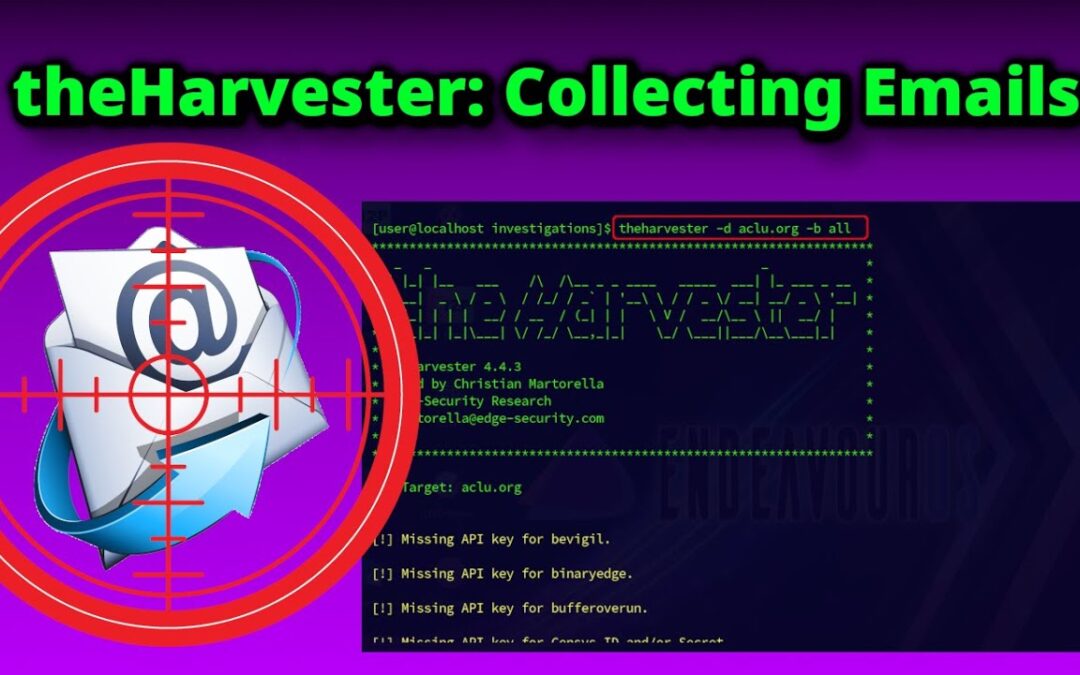
by Noel Saido | Jul 2, 2025 | Hacking, OSINT
When it comes to gathering email addresses during OSINT investigations, theHarvester is among the most efficient and beginner-friendly tools available. Not only does it do a great job of collecting email addresses, but it also excels at finding subdomains , sometimes...






