Introduction
In the fast-evolving world of cybersecurity, staying equipped with the latest tools is essential for ethical hackers and penetration testers. With new threats emerging daily, having the most reliable and efficient penetration testing tools at your disposal can mean the difference between a secure network and a data breach. This article will take a deep dive into the top 5 penetration testing tools for 2024, highlighting their key features, pros, and cons, and what makes them stand out in the cybersecurity landscape.
What to Look for in a Penetration Testing Tool
When choosing a penetration testing tool, several key features can help ensure you’re equipped for comprehensive and efficient testing:
- Comprehensive Scanning: The ability to conduct deep scans for various vulnerabilities.
- Ease of Use: Intuitive interfaces save time and reduce the learning curve.
- Frequent Updates: A tool that’s regularly updated keeps pace with the latest vulnerabilities.
- Customization and Automation: Scripting and automated capabilities can streamline the workflow.
- Community Support: An active community offers plugins, tutorials, and troubleshooting assistance.

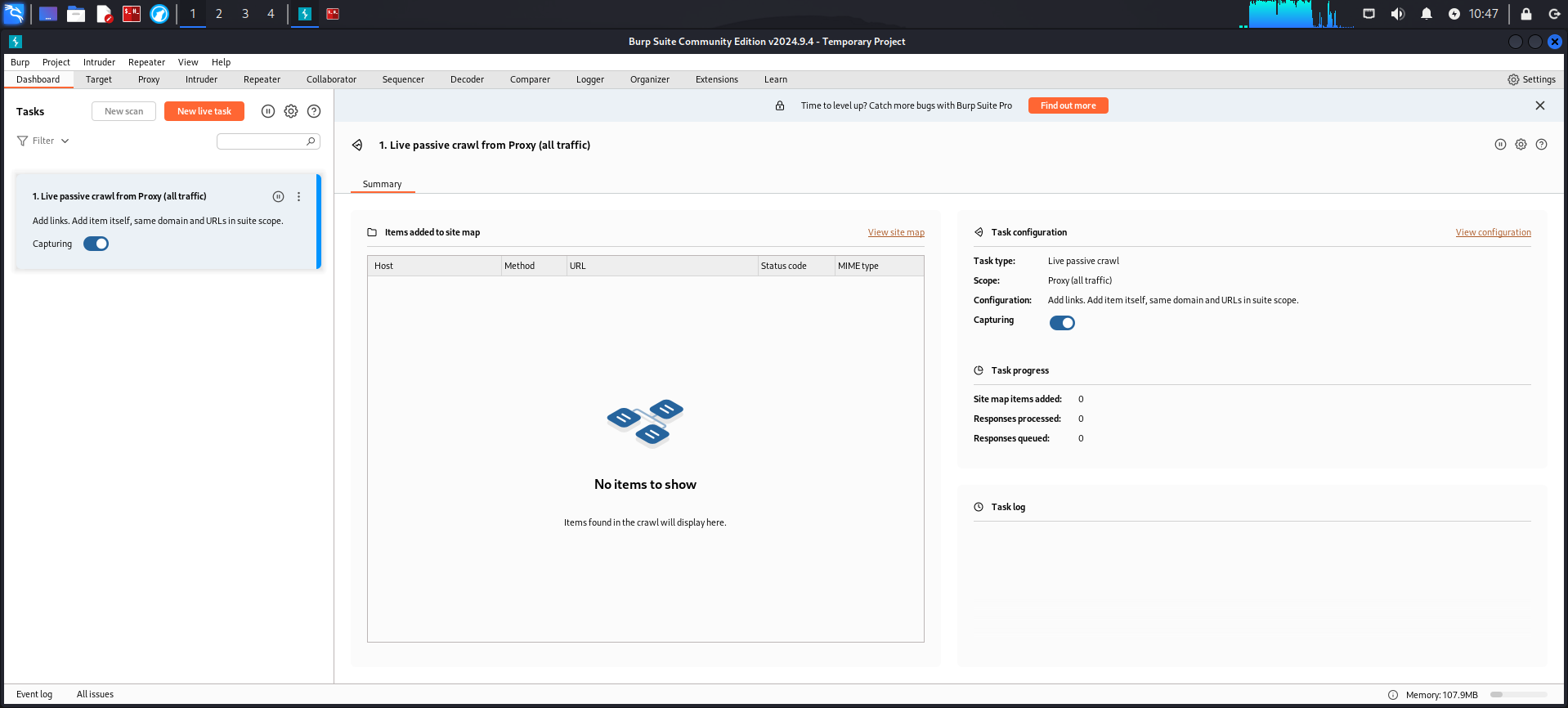
Tool 1: Burp Suite Pro
Overview
Burp Suite Pro by PortSwigger is widely considered the gold standard for web vulnerability assessment. It is known for its depth, flexibility, and user-friendly interface that appeals to both experienced and novice penetration testers.
Key Features
- Intercepting Proxy: Capture and modify web traffic between your browser and the target server.
- Automated Scanner: Finds common web vulnerabilities like XSS and SQL injection.
- Extensibility: Access a rich collection of custom extensions via the BApp Store.
- Reporting Tools: Create clear, detailed reports that can be easily shared.
Pros and Cons
Pros:
- Robust suite for both manual and automated testing.
- Highly customizable with extensive support for third-party plugins.
- Detailed documentation and user support.
Cons:
- Can be expensive, particularly for freelancers or smaller teams.
- Requires time to master all functionalities.
Use Case
Ideal for comprehensive web application testing and suited for professionals who need detailed analysis and flexibility.
Tool 2: Nmap
Overview
Nmap (Network Mapper) is a powerful, open-source network scanning tool used extensively for network discovery and security auditing. Its versatility and reliability make it a staple in any penetration tester’s toolkit.
Key Features
- Flexible Scanning Options: Scans for live hosts, open ports, and running services.
- Custom Scripting: The Nmap Scripting Engine (NSE) adds customized scanning capabilities.
- Cross-Platform: Runs seamlessly on Windows, macOS, and Linux.
Pros and Cons
Pros:
- Free and open-source.
- Highly adaptable with the use of scripts.
- Strong community support with frequent updates.
Cons:
- Command-line interface can be daunting for beginners.
- Advanced configurations may require in-depth knowledge.
Use Case
Perfect for preliminary reconnaissance and network mapping, especially for larger networks.

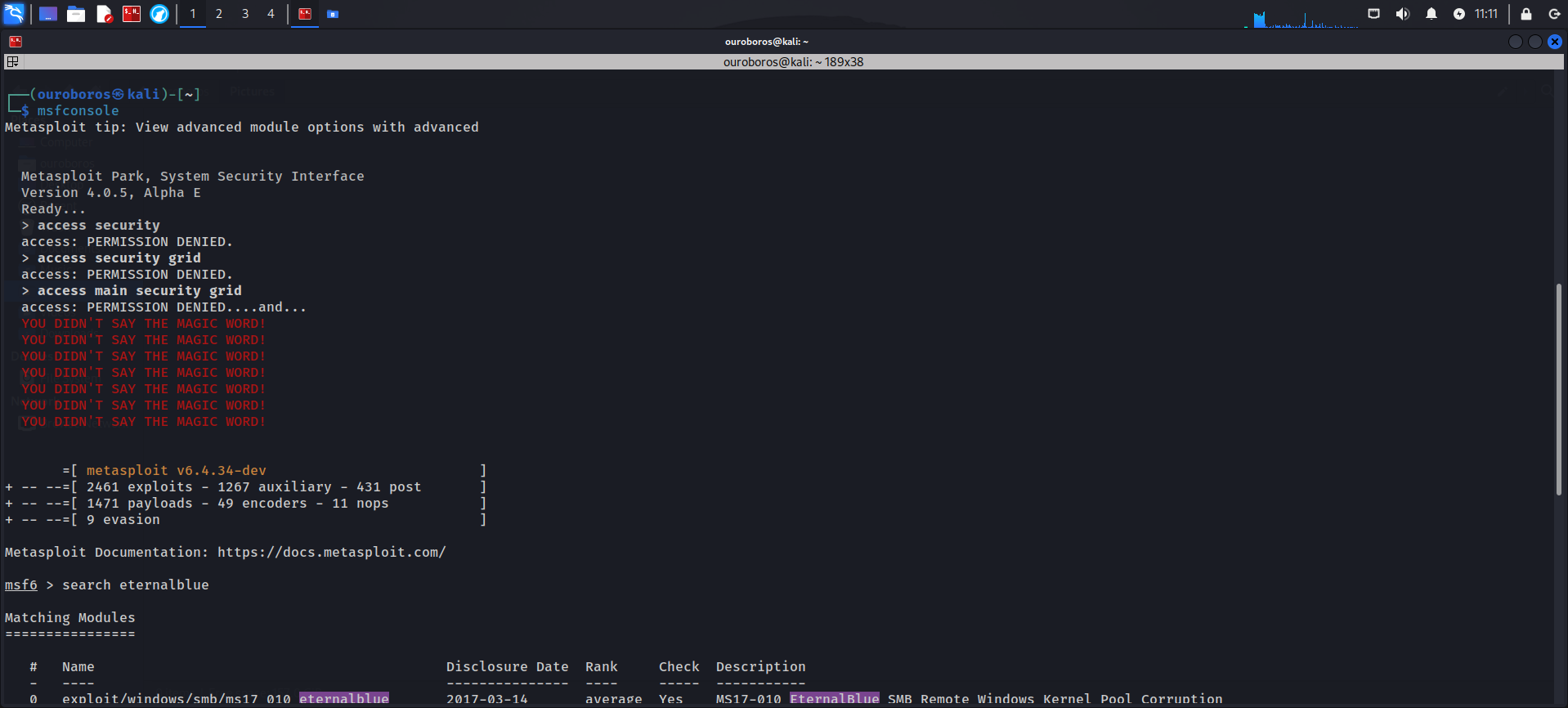
Metasploit Framework
Overview
Metasploit Framework is one of the most widely used tools for exploit development and penetration testing. Developed by Rapid7, it has set the benchmark for how vulnerabilities are tested and validated.
Key Features
- Extensive Exploit Library: Access thousands of exploits and payloads.
- Payload Customization: Create tailored payloads for unique testing scenarios.
- Integration: Pairs well with other tools like Nmap for a seamless workflow.
- Automated Exploitation: Simplifies the process of identifying and exploiting vulnerabilities.
Pros and Cons
Pros:
- Rich database of exploits for thorough testing.
- Open-source with a supportive community.
- Extensive documentation and tutorials.
Cons:
- May require substantial technical expertise.
- Newcomers might find the learning curve steep.
Use Case
Excellent for ethical hackers and penetration testers looking to demonstrate real-world vulnerabilities through controlled exploitation.
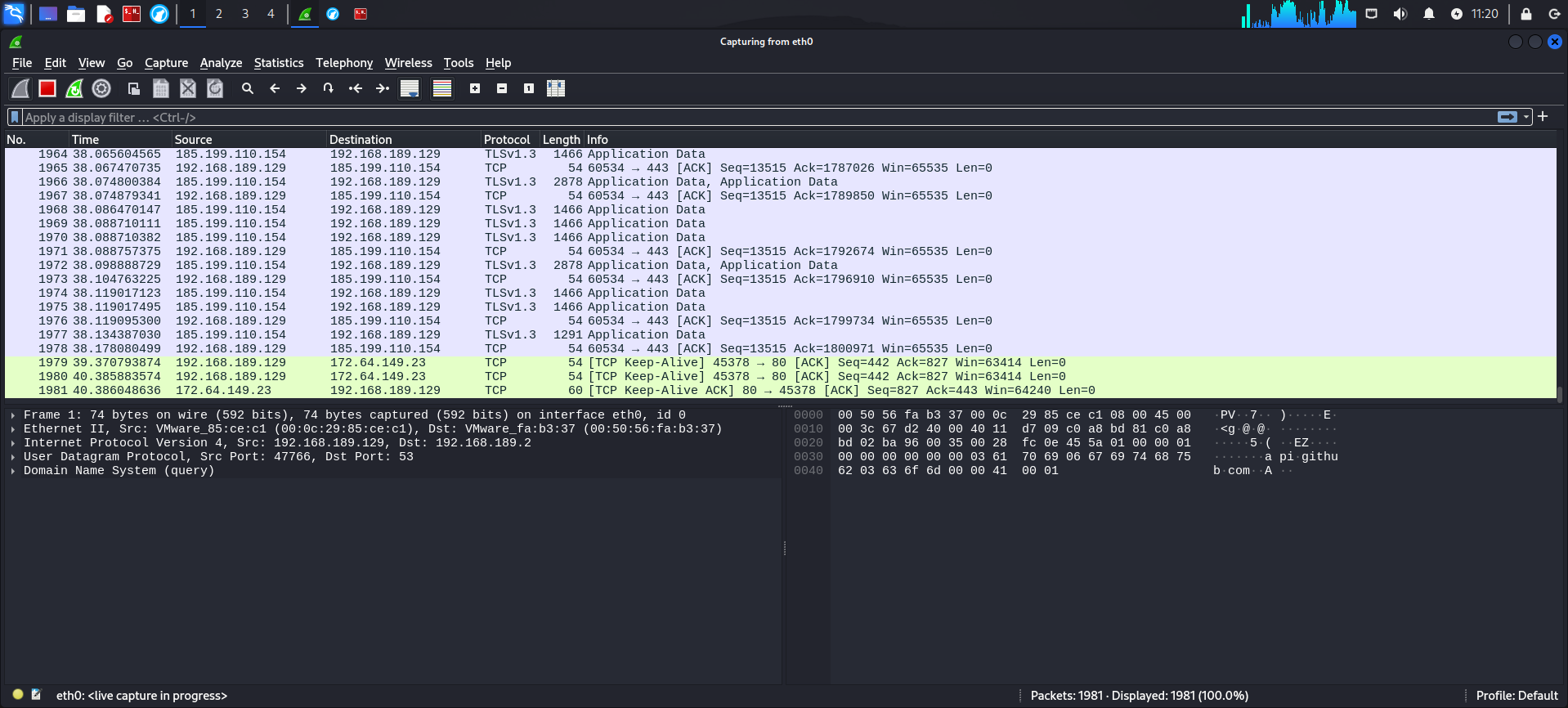
Tool 4: Wireshark
Overview
Wireshark is a leading network protocol analyzer that allows users to capture and analyze network traffic in real-time. It’s an essential tool for network administrators and penetration testers who need to inspect data packets closely.
Key Features
- Deep Packet Inspection: Provides comprehensive details about network protocols.
- Real-Time Capture: Monitors live traffic for immediate analysis.
- Wide Protocol Support: Recognizes hundreds of network protocols, with regular updates.
Pros and Cons
Pros:
- Free and open-source.
- Intuitive GUI that simplifies packet analysis.
- Excellent for detailed, protocol-level insights.
Cons:
- Can be overwhelming due to the sheer volume of data.
- Primarily passive; not used for active penetration tests.
Use Case
Best suited for situations requiring detailed network traffic analysis or troubleshooting network issues.
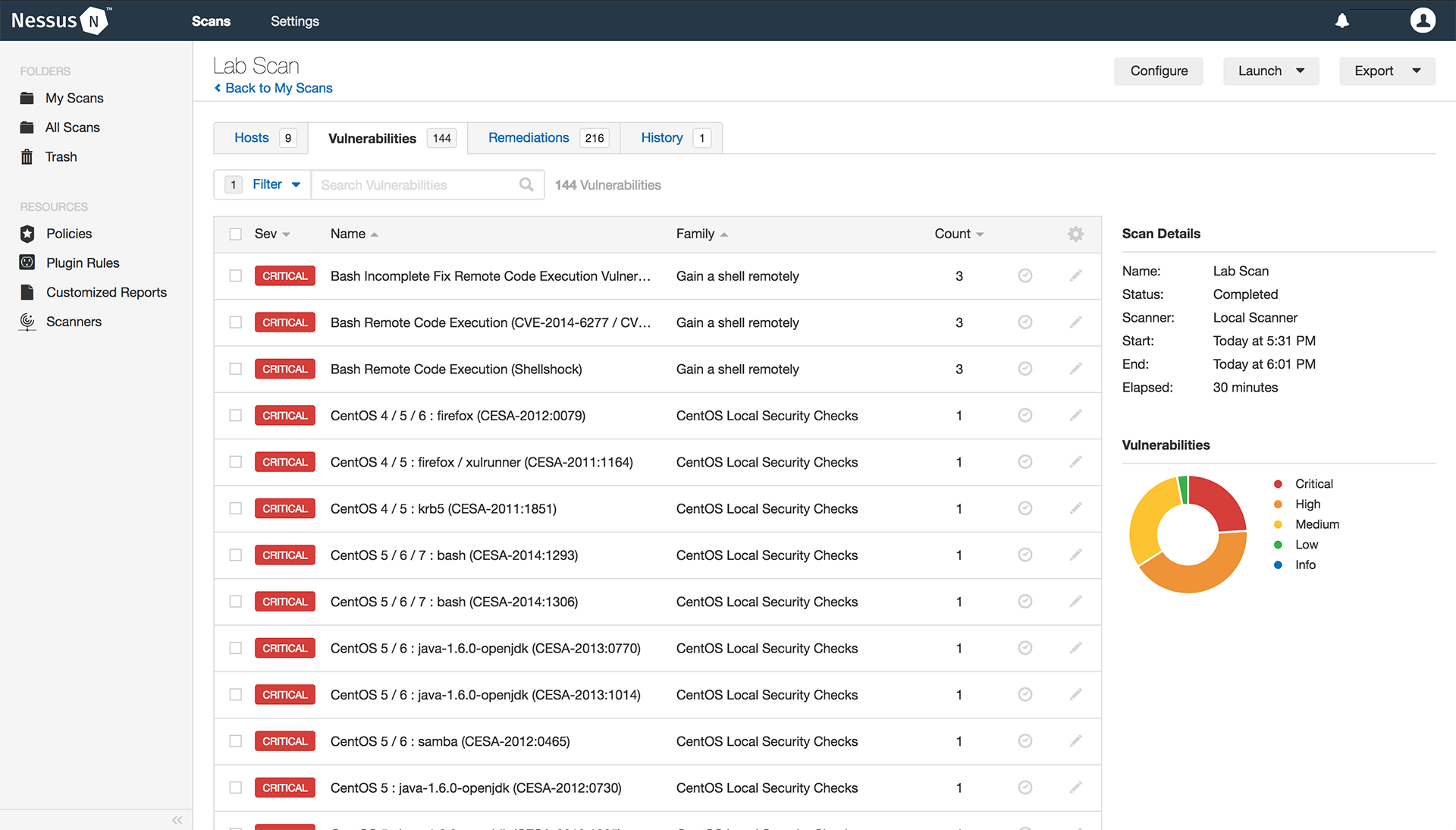
Tool 5: Nessus
Overview
Nessus by Tenable is a trusted tool for vulnerability assessment, known for its powerful scanning capabilities and ease of use. It’s suitable for cybersecurity teams of all sizes due to its comprehensive scanning and straightforward interface.
Key Features
- Large Plugin Library: Offers over 140,000 plugins for up-to-date vulnerability checks.
- User-Friendly Reports: Generates detailed, actionable reports that simplify remediation.
- Scheduling: Automates scans for routine checks and continuous monitoring.
Pros and Cons
Pros:
- Reliable and accurate scanning.
- Frequent plugin updates ensure coverage of the latest vulnerabilities.
- Scalable for various business sizes.
Cons:
- The free version has limited features.
- May require manual review for false positives.
Use Case
Ideal for thorough vulnerability scanning and compliance checks, particularly in enterprise environments.
Comparison Table
| Tools | Best For | Pros | Cons |
| Burp Suite Pro | Web application testing | Comprehensive, customizable | Expensive, steep learning curve |
| Nmap |
Network reconnaissance |
Free, powerful | CLI may be intimidating |
| Metasploit | Exploiting vulnerabilities | Large exploit library | Technical expertise needed |
| Wireshark | Packet analysis | Free, GUI | High data volume can overwhelm |
| Nessus | Vulnerability assessment | Reliable, user-friendly | Limited free version |
Honorable Mentions
- OWASP ZAP: An excellent open-source tool for web security testing, ideal for beginners and intermediate users.
- Aircrack-ng: A go-to for wireless network penetration testing.
- John the Ripper: A powerful password-cracking tool that helps assess password strength.
Final Thoughts
The right penetration testing tool depends on your projects’ specific needs and your expertise level. Burp Suite Pro is unmatched for comprehensive web vulnerability testing. Nmap and Wireshark are staples for network mapping and packet analysis, respectively. Metasploit Framework offers versatility for those focused on real-world exploitation, while Nessus is perfect for vulnerability assessments with detailed reporting.
FAQs
Q1: Which tool is best for beginners?
A1: OWASP ZAP and Wireshark are highly recommended for those starting out due to their ease of use and supportive communities.
Q2: Can these tools be used together?
A2: Yes, combining tools like Nmap for reconnaissance, Metasploit for exploitation, and Wireshark for packet analysis can create a comprehensive testing suite.
For a deeper dive into hacking tools, check out this informative video:





0 Comments